Supervisor
Administrator
- Apr 27, 2015
- 1,863
- 2,546
- 335
Update to 3.0.18.2 or newer
There are a few ways to protect yourself against this vulnerability.
Of those three, running TeamSpeak in a Sandbox is the safest way, as the Autostart should not get executed in there (I hope I'm right about this..)
Another way is to use TeamSpeak in either a Linux Virtual Machine (safe), or a seperate, only for TeamSpeak used Windows Virtual machine. If you use the Windows one, they can still get your TeamSpeak idendities and stuff like that. (combine your idendities and your favorite servery, and they may get a Serveradmin access pretty easily)
The third way would be the easiest one to use, unfortunately I didn't make that work, yet.
The last way is to check your startup directory every time you shut down your computer. You'll have to remember every file wich belongs in there, if you see any file wich does not, could be a potential virus/maleware/...
Checking whether this file is a link, is not reliable, as the attacker could easily drop two files to your computer, the virus, and the link to the virus in the startup. So checking file size is not a good option.
There are a few ways to protect yourself against this vulnerability.
- Sandbox
- a seperate Virtual machine only for TeamSpeak
a restricted, seperate Windows user accont only for TeamSpeak(looks like it's not gonna work becuase Windows security is SHIT)- checking your shell:startup directory every time before you shutdown your computer
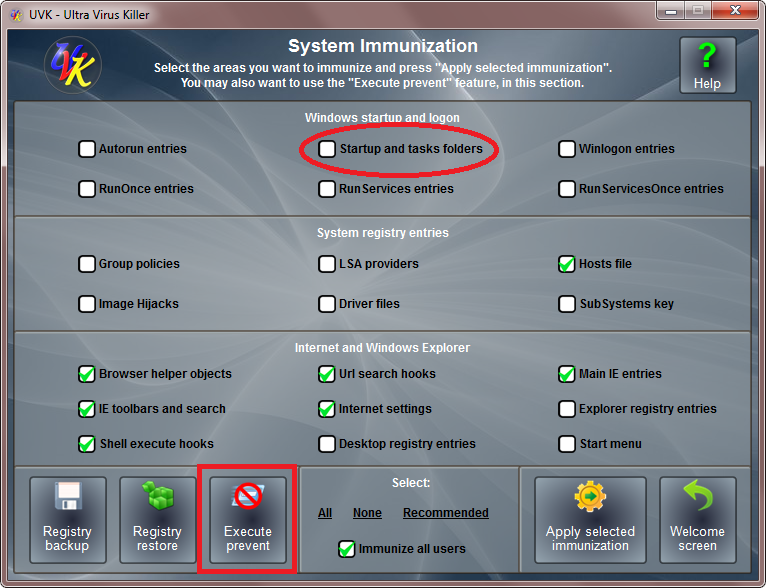
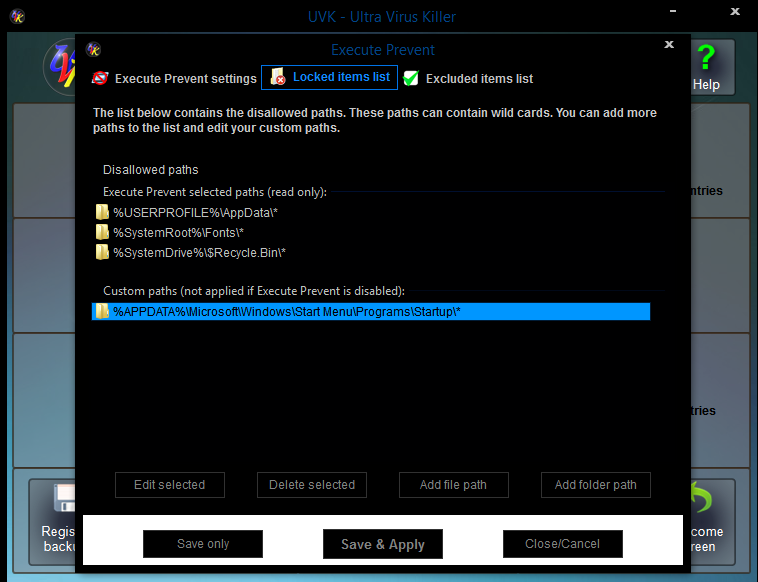
- use the programm provided here to lock your autostart directory
- TeamSpeak updated this severe issue very fast. Version 3.0.18.1 is available on the TeamSpeak website. Link to the news thread here
Keep in mind: a lot of users won't update within the next months if the hosting providers don't force them.
Of those three, running TeamSpeak in a Sandbox is the safest way, as the Autostart should not get executed in there (I hope I'm right about this..)
Another way is to use TeamSpeak in either a Linux Virtual Machine (safe), or a seperate, only for TeamSpeak used Windows Virtual machine. If you use the Windows one, they can still get your TeamSpeak idendities and stuff like that. (combine your idendities and your favorite servery, and they may get a Serveradmin access pretty easily)
The third way would be the easiest one to use, unfortunately I didn't make that work, yet.
The last way is to check your startup directory every time you shut down your computer. You'll have to remember every file wich belongs in there, if you see any file wich does not, could be a potential virus/maleware/...
Checking whether this file is a link, is not reliable, as the attacker could easily drop two files to your computer, the virus, and the link to the virus in the startup. So checking file size is not a good option.
Last edited: