- Apr 25, 2015
- 1,845
- 2
- 2,199
- 327
You walk into some hotel and are like "Man, I wonder if this WiFi is safe?"
Time to chase the mouse, as a cat to see how fast this things runs and maybe it has a nearby hiding hole?
Start with a console entry of 'arp -a'
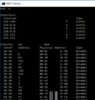
Notice in the image, below Interface, we see some dynamic IP addresses starting with 10.10, this is a start. How about we find the gateway perhaps?
Another favorite command to find the gateway is really simple, passing ipconfig to find "Gate" like
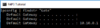
We can see the gateway is 10.10.0.1 which means that is, well the gateway and in this specific case since it is wireless, this is the wireless gateway of some sorts.
Also sometimes useful is running tracert, this should disclose the first hop which is sometimes your default gateway and other times not.
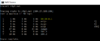
Now that we know this information, we can go inside a VM (Linux) to easier use a terminal with ZMap for example.
From the gateway itself, we already know 10.10.0.1 is how they're apparently assigning the dynamic IP addresses (arp info backs this up). A very bad @$* chart to reference for CIDR is available right here.
Anyway, the Nmap way is like so
You would want to write that out to a file though, so more like
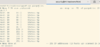
Well, let's charge through all this with ZMap.
Side-by-side comparison time using the below:
ZMap:
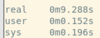
Nmap:
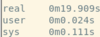
What about number of results for accuracy?

I am going to rerun the same commands to check for different results?

It is hard to be certain the above results are perfect because the network is uncontrolled by me, on this WiFi - there may be people disconnecting to impact my result comparisons.
It is easy to see that accuracy of these scans is not perfect but ZMap is quicker at discovery while Nmap is more accurate.
After scratching my chin on the accuracy part, I remembered I performed a side-by-side discovery scan table over here.
Masscan came out on top, so I am going to try that and see what comes back in the morning.
My takeaway is Nmap is accurate sometimes (typically), but Masscan is freaking amazing for accuracy plus overall discovery and Unicornscan and ZMap win in the quickness department.
Altogether, here is what I am finding to be a success:
Cat your 'where' file, you may try running this a couple times. You could end up filtered off, might have to disconnect and spoof your mac then reconnect to try another method.
At any rate, we are getting 10.162.9.200 the first time. Cool! So maybe 10.162.*.* is interesting since this goes away from our normal 10.10...
tl;dr expand you search deeper through the CIDR. Now, I am noticing when I Zmap sometimes my network activity ends up filtered out.
So, then I would wait a bit or reconnect like mentioned and try something more accurate on those like Nmap or Masscan, since Masscan is in my opinion faster and fairly accurate, I would do that next on the newly found CIDR like:
You will quickly generate a list of IP addresses (w/ port 80 open) on 10.162.*.* and I am already at 66 found and seconds later I am at 115! Masscan is lightning and fairly accurate.
Since Masscan is both accurate and fast, I would also recommend getting a feel for open ports across the net:
Eventually in more scanning, I find a 10.161 result! So we know they like 10.162 (minibar), 10.161 (misc so far), and apparently 10.10... is for WiFi peeps. Fair enough!
At further glance, 10.161.150.* is containing the most SSH (22) hosts.
Scanning can take time but eventually you may find out the network map (hence Nmap's name).
What tools you use makes a difference in accuracy and time. Know the tools and how to use them!
Keep in mind, this entire time I am only interested in discovery (uncovering the shadows). I have no interest in anything beyond discovering hosts on the network.
I think WiFi security is really important and "Just use a VPN" is not solution. Saying "just use a VPN" is like saying "Why didn't you just use your brakes?" - when a deer jumped in front of your car.
Just hotspot yourself over mobile (4G), and possibly use a VPN you build yourself.. w/ OpenVPN (unless you want to rebuild a whole VPN server software lol)..
Lastly, if you really just want to plow through a net and find all the most important pieces:
masscan -p22,3389 10.0.0.0/8
masscan -p22,3389 172.16.0.0/12
masscan -p22,3389 192.168.0.0/16
After that, you may know SSH/RDP hosts, then I'd go about checking for services like (port 80, 25, etc)! Have fun.. stay safe on any WiFi (or just do not connect on WiFi lol)..
Time to chase the mouse, as a cat to see how fast this things runs and maybe it has a nearby hiding hole?
Start with a console entry of 'arp -a'
Code:
arp -a
Notice in the image, below Interface, we see some dynamic IP addresses starting with 10.10, this is a start. How about we find the gateway perhaps?
Another favorite command to find the gateway is really simple, passing ipconfig to find "Gate" like
Code:
ipconfig | findstr "Gate"We can see the gateway is 10.10.0.1 which means that is, well the gateway and in this specific case since it is wireless, this is the wireless gateway of some sorts.
Also sometimes useful is running tracert, this should disclose the first hop which is sometimes your default gateway and other times not.
Code:
tracert r4p3.netNow that we know this information, we can go inside a VM (Linux) to easier use a terminal with ZMap for example.
From the gateway itself, we already know 10.10.0.1 is how they're apparently assigning the dynamic IP addresses (arp info backs this up). A very bad @$* chart to reference for CIDR is available right here.
Anyway, the Nmap way is like so
Code:
nmap -sn -PE 10.10.*.*You would want to write that out to a file though, so more like
Code:
nmap -sn -PE 10.10.*.* -oG pinged.txtWell, let's charge through all this with ZMap.
Code:
zmap --probe-module=icmp_echoscan 10.10.0.0/16 -o zmap_pingSide-by-side comparison time using the below:
Code:
time zmap --probe-module=icmp_echoscan 10.10.7.0/24 -o zmap_ping
time nmap -sn -PE 10.10.7.* -oG nmap_pingZMap:
Nmap:
What about number of results for accuracy?
I am going to rerun the same commands to check for different results?
It is hard to be certain the above results are perfect because the network is uncontrolled by me, on this WiFi - there may be people disconnecting to impact my result comparisons.
It is easy to see that accuracy of these scans is not perfect but ZMap is quicker at discovery while Nmap is more accurate.
After scratching my chin on the accuracy part, I remembered I performed a side-by-side discovery scan table over here.
Masscan came out on top, so I am going to try that and see what comes back in the morning.
My takeaway is Nmap is accurate sometimes (typically), but Masscan is freaking amazing for accuracy plus overall discovery and Unicornscan and ZMap win in the quickness department.
Altogether, here is what I am finding to be a success:
Code:
zmap -p80 10.0.0.0/8 -o where.txtCat your 'where' file, you may try running this a couple times. You could end up filtered off, might have to disconnect and spoof your mac then reconnect to try another method.
At any rate, we are getting 10.162.9.200 the first time. Cool! So maybe 10.162.*.* is interesting since this goes away from our normal 10.10...
tl;dr expand you search deeper through the CIDR. Now, I am noticing when I Zmap sometimes my network activity ends up filtered out.
So, then I would wait a bit or reconnect like mentioned and try something more accurate on those like Nmap or Masscan, since Masscan is in my opinion faster and fairly accurate, I would do that next on the newly found CIDR like:
Code:
masscan -p80 10.162.0.0/16You will quickly generate a list of IP addresses (w/ port 80 open) on 10.162.*.* and I am already at 66 found and seconds later I am at 115! Masscan is lightning and fairly accurate.
Since Masscan is both accurate and fast, I would also recommend getting a feel for open ports across the net:
Code:
masscan -p80 10.0.0.0/8 -oG web
masscan -p22 10.0.0.0/8 -oG ssh
masscan -p3389 10.0.0.0/8 -oG winEventually in more scanning, I find a 10.161 result! So we know they like 10.162 (minibar), 10.161 (misc so far), and apparently 10.10... is for WiFi peeps. Fair enough!
At further glance, 10.161.150.* is containing the most SSH (22) hosts.
Scanning can take time but eventually you may find out the network map (hence Nmap's name).
What tools you use makes a difference in accuracy and time. Know the tools and how to use them!
Keep in mind, this entire time I am only interested in discovery (uncovering the shadows). I have no interest in anything beyond discovering hosts on the network.
I think WiFi security is really important and "Just use a VPN" is not solution. Saying "just use a VPN" is like saying "Why didn't you just use your brakes?" - when a deer jumped in front of your car.
Just hotspot yourself over mobile (4G), and possibly use a VPN you build yourself.. w/ OpenVPN (unless you want to rebuild a whole VPN server software lol)..
Lastly, if you really just want to plow through a net and find all the most important pieces:
masscan -p22,3389 10.0.0.0/8
masscan -p22,3389 172.16.0.0/12
masscan -p22,3389 192.168.0.0/16
After that, you may know SSH/RDP hosts, then I'd go about checking for services like (port 80, 25, etc)! Have fun.. stay safe on any WiFi (or just do not connect on WiFi lol)..